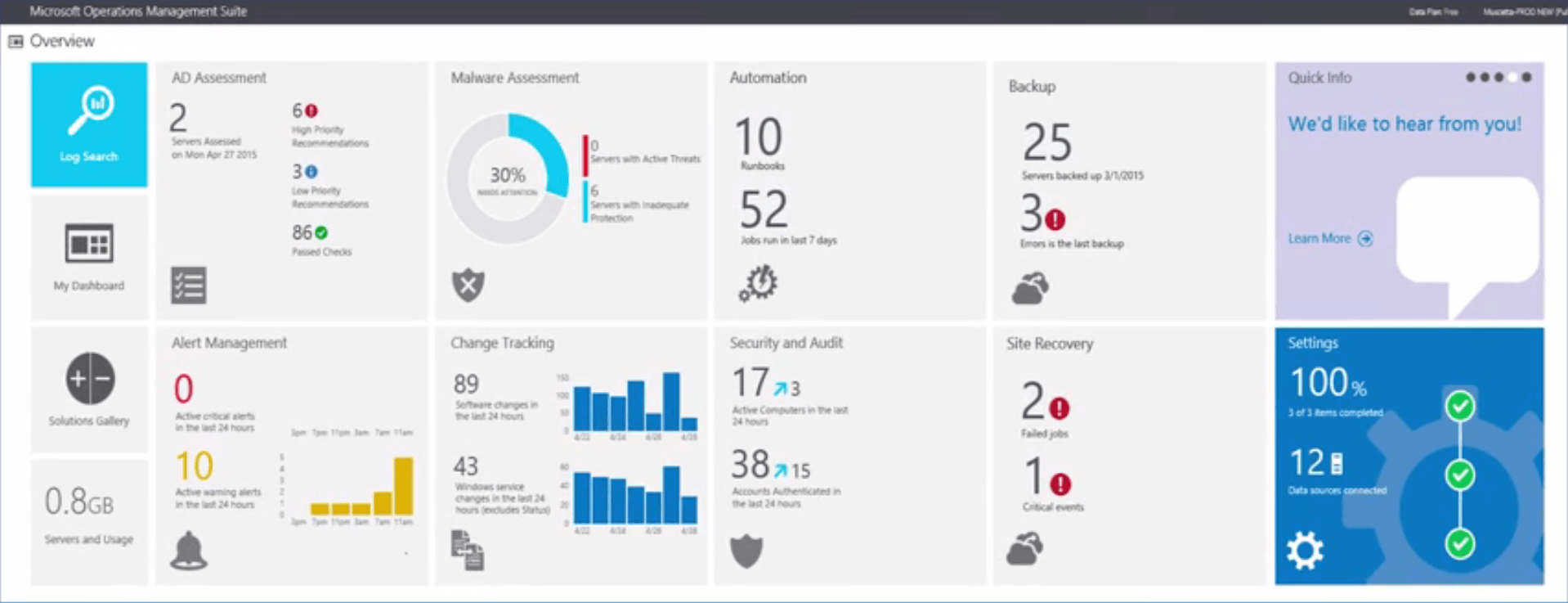
In the beginning there was…nothing
Microsoft Azure Stack is not something I could build and run on my desktop like my Configmgr lab, which runs on my W10 desktop while I use it for work as well. I had to decide if I wanted to spend the money on a server or wait for the hardware to fall into my hands. Because I saw this a real opportunity to learn something that would be valuable to my customers and myself, and because my wife…I mean CFO, approved the request I purchased the individual parts to build my own server for my home lab.
Having had a server in my home lab previously I knew of the drawbacks. Noise and heat. Lots of both. Doing a customer demo when you are sweating and they cannot hear you makes doing a demo difficult. That meant I had to meet the hardware requirements of Azure Stack, and it had to be quiet and cool.
And then there was…
After lots of research, I ordered all of my hardware. Things have not changed much since I got my A+ back in 1995, thankfully. And yes it did boot the first time I powered it on. I won’t get into the hardware details but you can take a stab at it based on the images.





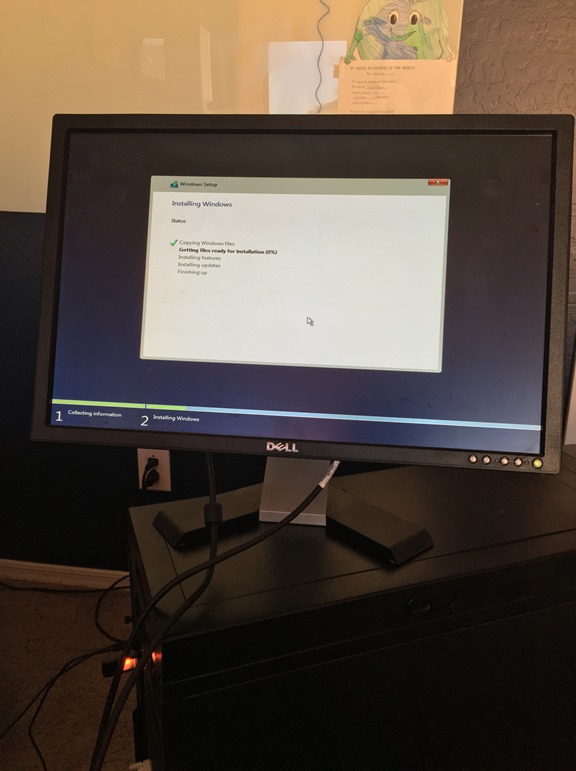

You can download the bits for Azure Stack here, and this is a link to the instructions on how to setup Azure Stack. The instrcutions assume you have met the list of hardware requirements listed here and other requirements listed here.
Since I had a few hours while it installed, I went for a run out at Goldmine trail, which is about 20 minutes from me.
The install threw an error and I had to go visit a customer to upgrade them to Configmgr current branch, so it would have to wait until I got back. At least, my server was nice and warm at home.
Back at home. My install on the base OS did not work. It complained that my time was off. There is no UTC/local time setting in my BIOS and here in AZ we don’t do DST, so today we are equal to MST. All times and time zones matched so after talking to a couple Azure TSP’s I decided to install using the VHD method, which worked, not sure why but it did. It only took about two hours to install instead of the estimated four.
After returning from the northwest…
I completed the setup in my lab and it was pretty painless to get running. I have since reinstalled it on the same system, starting from scratch.
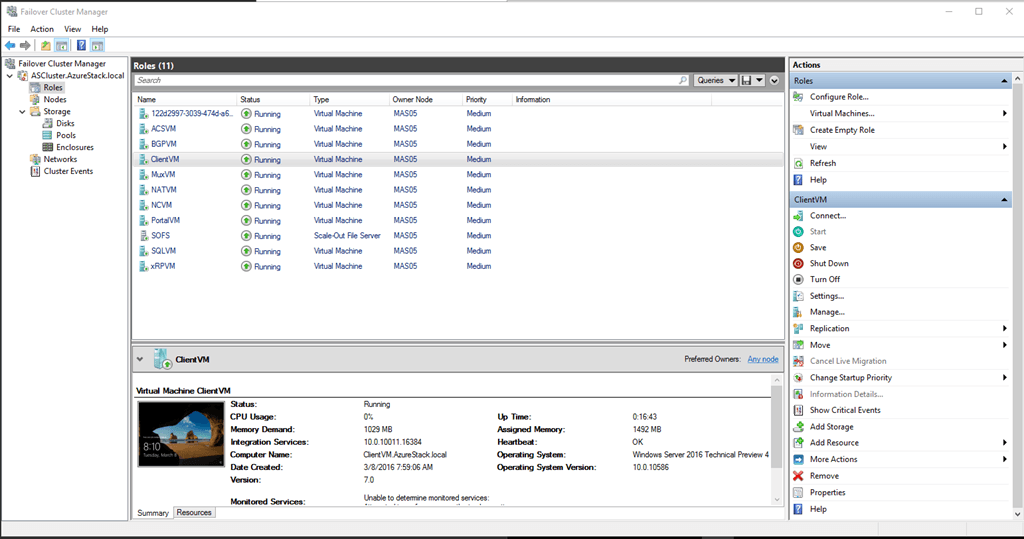
When setup is complete and you run Failover Cluster Manager, or Hyper-V Manager, you will see the list of VM’s running. If the PowerShell script throws an error during setup, fix the issue and then run the script again and it will pick up where it left off. At the end you should have something like this.
Azure Stack VMs
Here is a breakdown of each VM you have running once the installation of Azure Stack has completed:
ADVM Virtual machine that hosts Active Directory, DNS, and DHCP services for Microsoft Azure Stack. These infrastructure foundational services are required to bring up the Azure Stack as well as the ongoing maintenance.
ACSVM Virtual machine that hosts the Azure Consistent Storage services. These services run on the Service Fabric on a dedicated virtual machine.
MuxVM Virtual machine that hosts the Microsoft software load balancer component and network multiplexing services.
NCVM Virtual machine that hosts the Microsoft network controller component, which is a key component of the Microsoft software-defined networking technology. These services run on the Service Fabric on this dedicated virtual machine.
NATVM Virtual machine that hosts the Microsoft network address translation component. This enables outbound network connectivity from Microsoft Azure Stack.
xRPVM Virtual machine that hosts the core resource providers of Microsoft Azure Stack, including the Compute, Network, and Storage resource providers.
SQLVM Virtual machine that hosts SQL Servers which is used by various fabric services (ACS and xRP services).
PortalVM Virtual machine that hosts the Control Plane (Azure Resource Manager) and Azure portal services and various experiences (including services supporting admin experiences and tenant experiences).
ClientVM Virtual machine that is available to developers for installing PowerShell, Visuall Studio, and other tools.
And…Storage services in the operating system on the physical host include:
ACS Blob Service Azure Consistent Storage Blob service, which provides blob and table storage services. SoFS Scale-out File Server. ReFS CSV Resilient File System Cluster Shared Volume.Virtual Disk, Storage Space, and Storage Spaces Direct are the respective underlying storage technology in Windows Server to enable the Microsoft Azure Stack core storage resource provider.
Here is a graphic representation of the VM’s and services.

Manually Shutting Down Azure Stack
If you need to manually shutdown and startup the VM’s this is the recommended order:
ClientVM, PortalVM, xRPVM, ACSVM, MuxVM, NCVM, SQLVM
Hyper-V will shut down the other three for you as you shutdown your server. The start order is reverse. If you need to manually shut down, after you start the VM’s ensure that all the services on xRPVM are running and happy, if it isn’t you will have issues since it hosts the core of the Azure Stack resources.
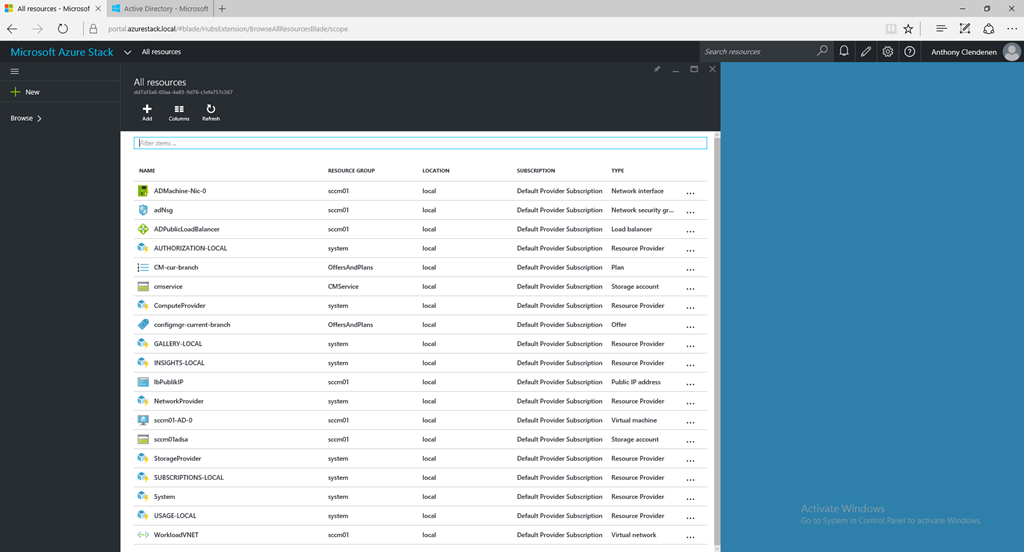
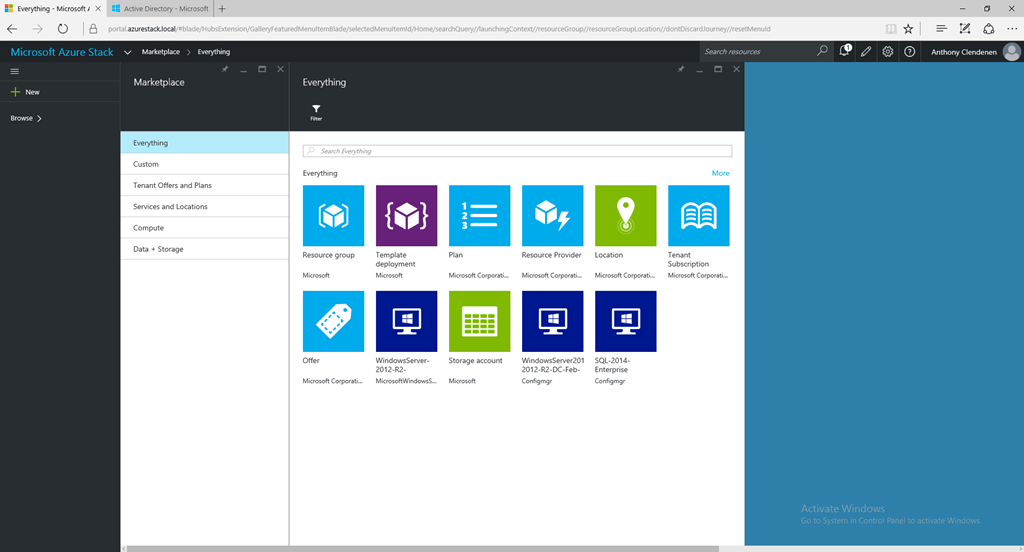
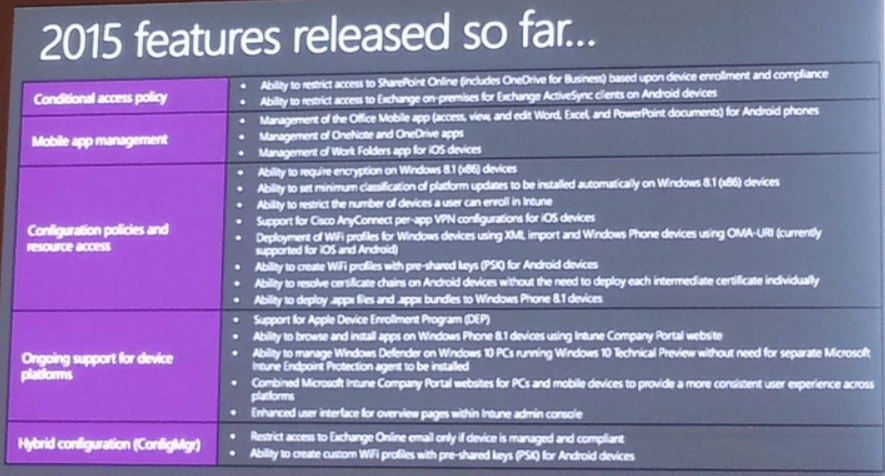
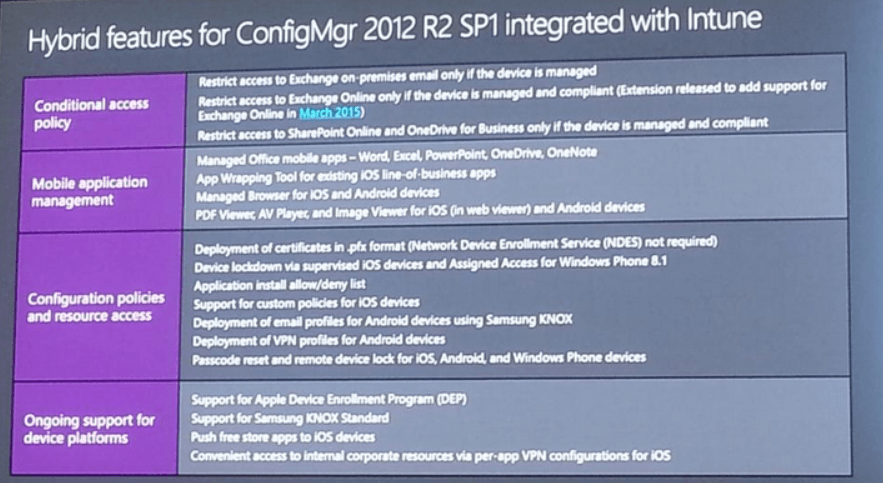
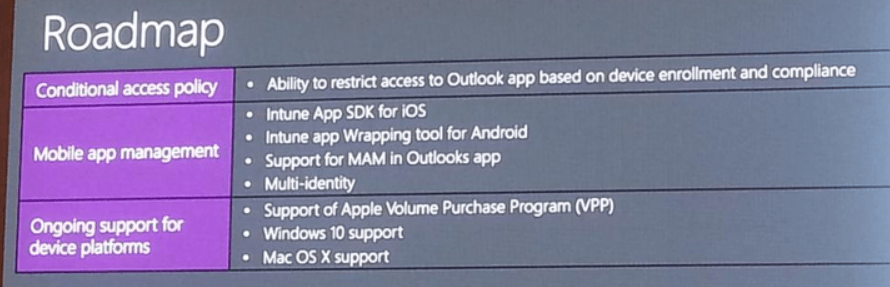
Azure Stack Portal
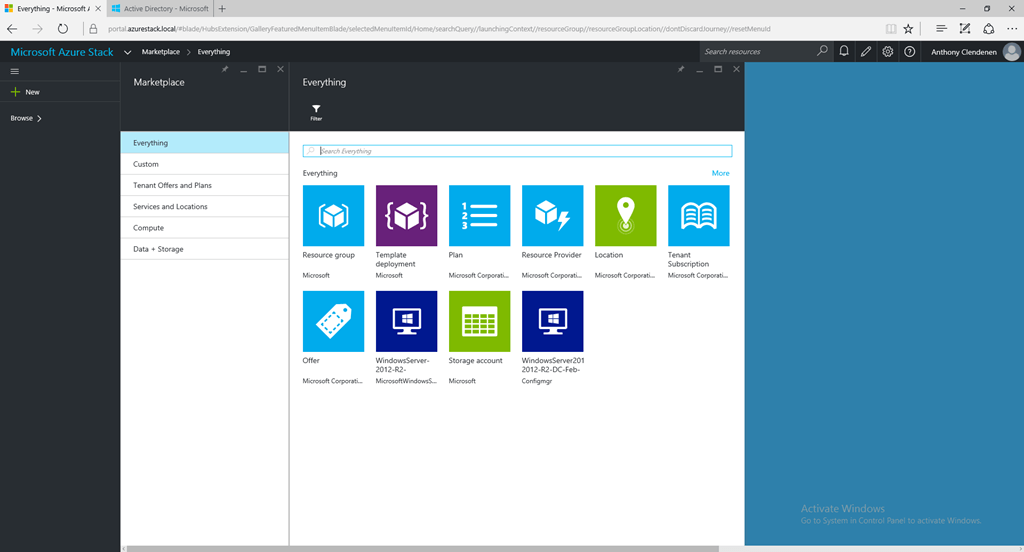
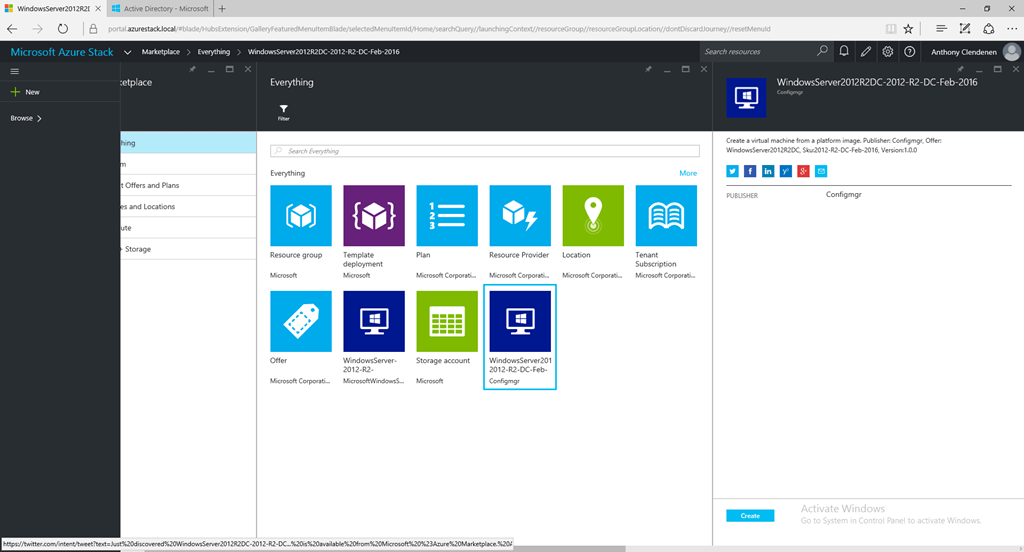
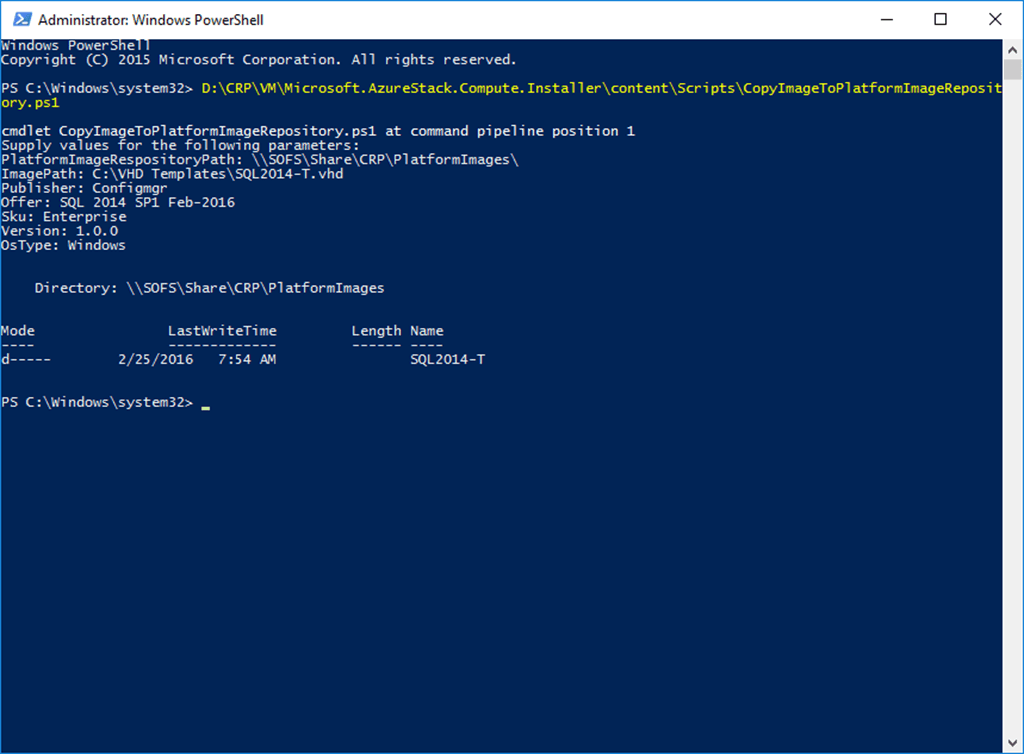
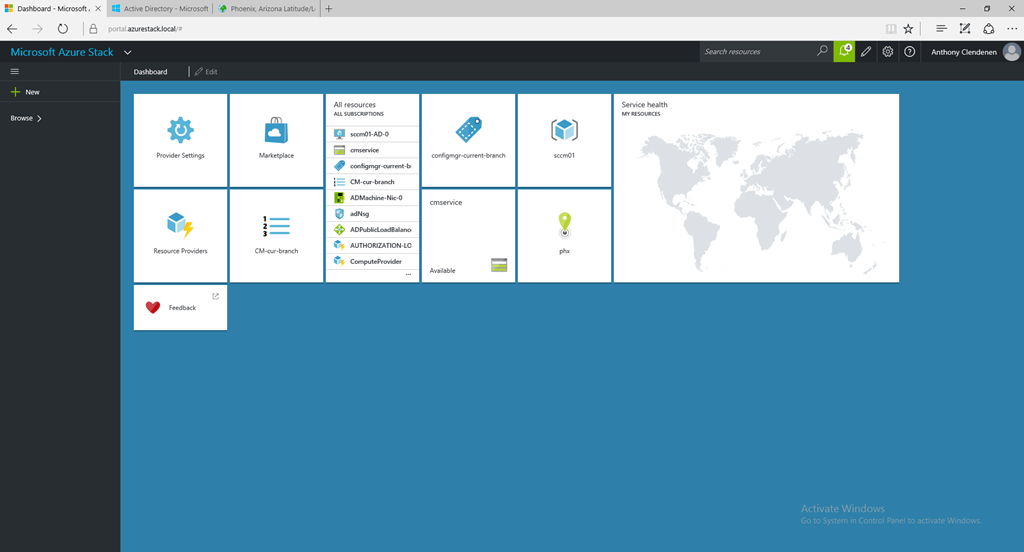
This is a set of images on the ClientVM. Showing the portal view, then the ARM templates resources imported from GitHub, then as it appears in the marketplace. Then a custom built VM template imported into the marketplace, using PowerShell to add a SQL 2014 custom VM into the platform image repository (PIR), and finally the custom SQL 2014 VM listed in the marketplace.