My top 10 most important announcements so far at Ignite. Ranked from most important to least importance, as it pertains to me.
- Technical preview of Configmgr vNext available now with SCEP
- Service pack for SCCM 2012 due next week
- Announced Azure Stack – Replacing Azure Pack for on-prem Azure services Deploying Azure in Your Datacenter
- Roadmap for Configmgr and Intune
- The Microsoft Operations Management Suite (OMS)
- Microsoft Advanced Threat Analytics
- Power BI in SCCM
- Detecting Anomalous Sign-Ins with EMS
- Windows 10 Device Guard
- The New Outlook App: A Modern Standard for Secure E-mail
Configmgr vNext Technical Preview
New features in today’s Technical Preview include:
- Support for Windows 10 upgrade with OS deployment task sequence – In addition to providing support for existing wipe-and-load (refresh) scenarios, the ConfigMgr Technical Preview includes enhanced upgrade support with in-place upgrade to Windows 10.
- Support for installing Configuration Manager on Azure Virtual Machines – Similar to how you can install ConfigMgr on Hyper-V today, you can now run ConfigMgr in Azure VMs. This provides flexibility to move some or all of your datacenter server workloads to the cloud with Azure.
- Ability to manage Windows 10 mobile devices via MDM with on-premises Configuration Manager infrastructure – With this new option, you can manage Windows 10 mobile devices using ConfigMgr integrated with Microsoft Intune (hybrid) without the need to store your data in the cloud. This is especially helpful for managing devices that are unable to connect to the Internet such as Windows IoT/Embedded devices. So go ahead and try it out – you can enroll devices, set policies, and wipe/retire devices today with more functionality to be added in the future to manage all of your Windows 10 devices with MDM.
Service Pack for Configmgr 2012 (next week)
Next week, Microsoft will also be releasing service packs for Configuration Manager 2012 and 2012 R2 to customers. These will deliver full compatibility with existing features for Windows 10 deployment and management as well as several other features, including:
- App-V publishing performance – Improved performance that reduces the time required for apps to display after the first logon for non-persistent VDI environments.
- Scalability improvements – Increased hierarchy scale to 600K and primary/standalone site scale to 150K.
- Content distribution improvements – Improved data transfer reliability for slow and latent networks, and also improved scale and performance for pull distribution points (DP).
- Native support for SQL Server 2014 – Added native support for SQL Server 2014 to enable site installation and recovery using SQL Server 2014.
- Hybrid features – Added a large number of hybrid features for customers using ConfigMgr integrated with Microsoft Intune (hybrid). Some of the features that you can expect to see in this release include conditional access policy, mobile application management, and support for Apple Device Enrollment Program (DEP).
Finally, for SCCM 2007:
- System Center Configuration Manager 2007 (SP2, R2, and R3) support for the management of Windows 10 is coming via a compatibility pack in Q4 2015 (Note: OS and client deployment will not be supported).
- An update for the Microsoft Deployment Toolkit (MDT) in Q3 2015 that will deliver support for Windows 10.
Azure Stack
This is Azure running in your own datacenter.
Azure Stack transforms your datacenter infrastructure into automated resource pools that can be tailored to application service levels. This means that your app owners can quickly consume standardized IaaS/PaaS services using the same self-service experience as Azure – and they can do it through a consistent app platform that spans on-premises and Azure.
This makes containers and Hyper-V containers and Nano server much more interesting.
Four other things to consider with Azure Stack:
- Cloud-inspired infrastructure
Azure Stack is built on a great heritage of technology (Azure, Windows Server, System Center) and it delivers reliable, software-defined infrastructure, that’s proven at hyper scale. - On-demand infrastructure extensions
With Azure Stack you have access to Azure’s bottomless scale and elasticity – without affecting your ongoing on-prem security protocols or performance. - Cloud-consistent service delivery
Enable your developers and end-users to productively consume software-defined infrastructure using the same intuitive self-service experience as Azure. The result is faster time-to-market with composable IaaS/PaaS services that can be deployed wherever you need them (on-prem, hosted, or Azure). - Cloud-optimized application platform
Windows Server and Azure deliver a consistent app platform for next-generation apps. This empowers your developers to build apps for any environment, and those apps can be used in any cloud without having to modify, rewrite or reconfigure code.
Roadmap for Configmgr 2012
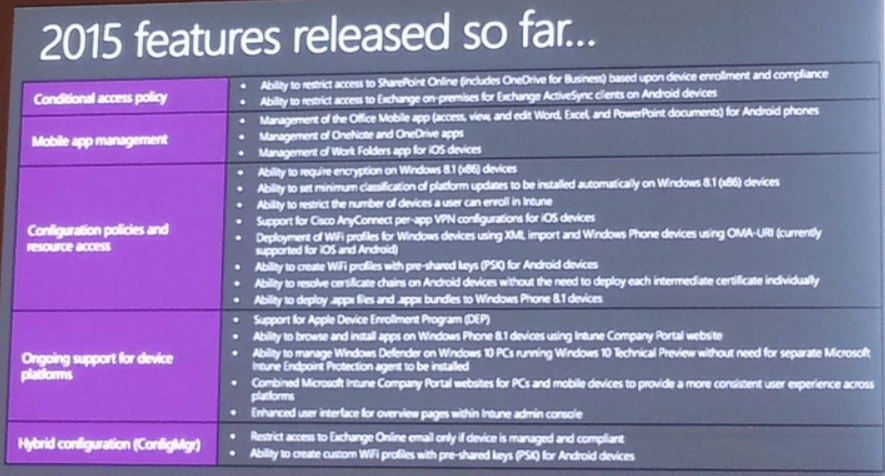
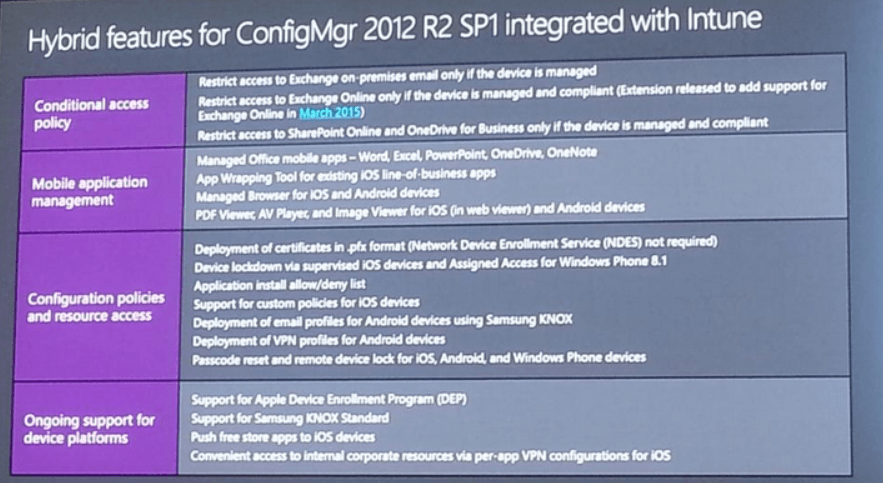
Conditional Access Policy
- Restrict Access to Exchange on-premise email only if the device is managed
- Restrict access to Exchange Online only if the device is managed and compliant (Extension released to add support for Exchange Online in March 2015)
- Restrict access to SharePoint Online and OneDrive for Business only if the device is managed and compliant
Mobile Application Management
- Managed Office mobile apps – Word, Excel, PowerPoint, OneDrive, OneNote
- App Wrapping Tool for existing iOS line-of-business apps
- Managed Browser for iOS and Android devices
- PDF Viewer, AV Player, and Image Viewer for iOS (in web viewer) and Android devices
Configuration Policies and Resources Access
- Deployment of certificates in .pfx format (Network Device Enrollment Service not required)
- Device lockdown via supervised iOS devices and Assigned Access for Windows Phone 8.1
- Application install allow/deny list
- Support for custom policies for iOS devices
- Deployment of email profiles for Android devices using Samsung KNOX
- Deployment of VPN profiles for Android devices
- Passcode reset and remote device lock for iOS, Android, and Windows Phone devices
Ongoing Support for Device Platforms
- Support for Apple Device Enrollment Program (DEP)
- Support for Samsung KNOX Standard
- Push free store apps to iOS devices
- Convenient access to internal corporate resources via per-app VPN configurations for iOS
Futures
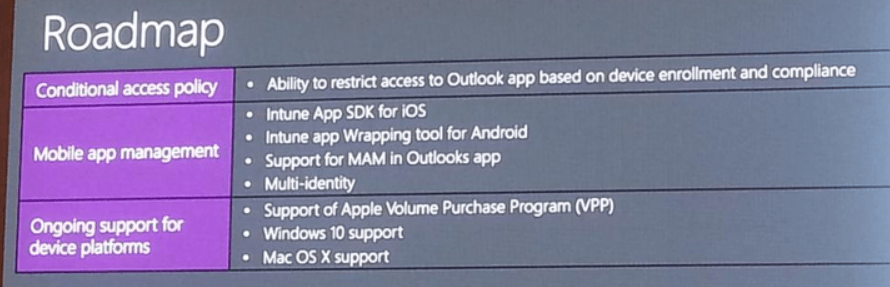
Conditional access policy
- Ability to restrict access to Outlook app based on device enrollment and compliance
Mobile app management
- Intune app SDK for iOS
- Intune app wrapping tool for Android
- Support for MAM in Outlook apps
- Multi-Identity
Ongoing support for device platforms
- Support for Apple Volume Purchase Program (VPP)
- Windows 10 support
- Mac OS X support
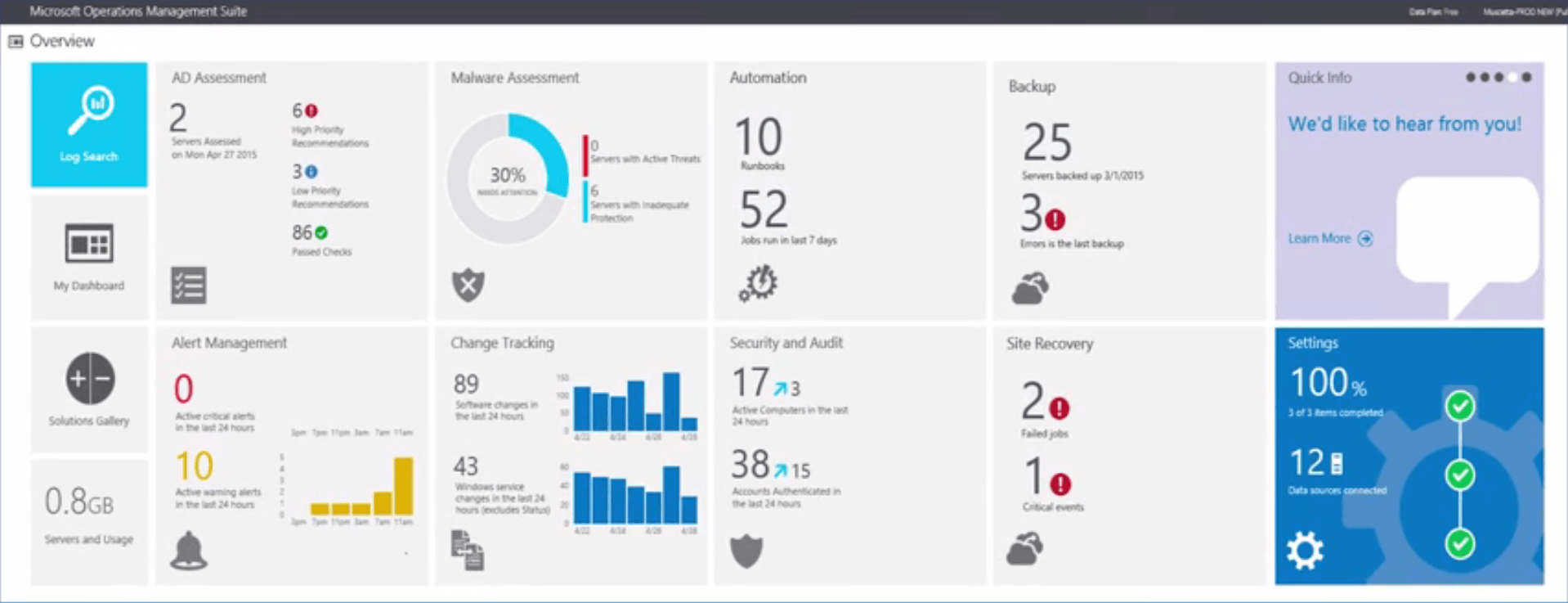
Microsoft Operations Management Suite
A new tool for managing your on-premise datacenter and cloud environment from a single view.
Having a hybrid infrastructure that is “pretty good” is not enough. This is a solution that creates a hybrid infrastructure that is great. Now you can manage Azure or AWS, Windows Server or Linux, VMware or OpenStack – all with a cost-effective, all-in-one cloud IT management solution.
With OMS you’re going to see six big benefits right out of the box:
- Log Analytics:
Now you can collect and search across multiple machine data sources and identify the root cause of any operational issues (learn more here). - Availability:
Integrated recovery is enabled for all your servers and apps – no matter where they reside. - Automation:
Complex and repetitive operations are orchestrated for more efficient and cost-effective hybrid cloud management. - Security:
You can identify malware status and missing system updates, and collect security-related events to perform forensic, audit and breach analysis. - Extending System Center:
OMS combines with System Center to do some amazing things. For example, OMS extends its capability to deliver a full hybrid management experience across any datacenter or cloud. - Hybrid & Open:
We recognize that your organization is no longer housed in just a single datacenter. That’s why OMS can manage your hybrid cloud no matter what topology or technology you’re using – and, of course, it works seamlessly with our existing on-prem infrastructure.
View a video of OMS in action here.
The pricing today is available as an addition to your Azure subscription with pay-as-you-go pricing for the features you need. In July you will also be able to add it to your System Center licensing as a step-up pricing.
Microsoft Advanced Threat Analytics
Microsoft Advanced Threat Analytics is an on-premises product to help IT organizations protect their enterprise from advanced targeted attacks by automatically analyzing, learning, and identifying normal and abnormal entity (user, devices, and resources) behavior through Active Directory, the identity management technology used by most enterprises. It also detects known malicious attacks and security issues using security research work. ATA provides clear and relevant threat information on a simple convenient feed, helping IT security professionals to focus on what is important. You can learn more by visiting the Microsoft Advanced Threat Analytics page. Read today’s blog post from our engineering team.
Power BI for Configmgr
This combines two great things that are long overdue being paired together: Power BI and System Center Configuration Manager. This combination gives configmgr admins the ability to monitor and report on software update and endpoint protection compliance in their organization, along with other compliance data from baseline configurations, configuration items, software deployments, so on.
This is the dashboard every CISO in the world would want to have and use. In a single place you can now get a view of mobile device compliance with corporate policies, PC compliance with security updates, and malware encounters across the entire enterprise. The Power BI dashboard enables you to drill into a wide variety of reports to identify trends and correlations, as well as use the Power BI Q&A feature to quickly identify any user data that may be at risk.
By integrating with Power BI, you are able to make this data accessible and consumable by IT organizations everywhere and enable IT Pros to unlock powerful new ways to work with, learn from, and take action on their data.
This is an incredible example of the truly vast benefits of using an integrated solution for PC and mobile device management.
The benefits include
- This dashboard is massively helpful for monitoring and reporting on software updates and endpoint protection compliance for your organization.
- The interface allows you to identify correlations and gain insight into management and security trends.
- With the Power BI Q&A feature you can immediately get answers to natural language questions about software updates and malware data.
- Now you can wallow in the data and see insights that would have been impossible to spot before.
Get started with Power-BI and Configmgr here.
Detecting Azure Anomalous Logins with EMS
This adds analytics-driven security controls to the security you already have. Azure Active Directory’s Machine Learning based anomaly detection reports analyze login patterns to detect irregular activity
- Azure AD is constantly monitoring user authentication behavior to detect anomalies that might be indicative of identity compromise.
- This constant monitoring allows IT to quickly identify attacks to their organization and take action.
- Having Azure AD do the heavy lifting of nonstop user authentications monitoring allows IT to focus on the mission-critical task of remediation.
- You can catch these compromised accounts and stop attacks!
Device Guard for Windows 10
Device Guard demands that every app attempting to access your network has to be proven safe before it enters, and, even more importantly, Device Guard’s capabilities are protected in an unprecedented way that uses virtualization to protect itself even in the event that the Windows Kernel is fully compromised.
For this reason, Device Guard can block zero day exploits and unknown malware threats because it isn’t dependent on the latest AV signatures or behavior monitoring. It also neutralizes common intrusion workarounds because Device Guard protects users even when they have full admin privileges.
- This feature is ideal for a very wide range of devices, like PoS’s, ATM’s, and any other assets that serve a critical business function and contain sensitive data.
- As noted above: It blocks zero day exploits and protects users with admin privileges.
- This enables IT to provide a much higher level of assurance that malware will not be running on devices.
Coming soon
New Outlook Using MAM
This gives IT control of which apps have access to business data and can share that data. Now end-users no longer need two apps for the same purpose (e.g. one for personal and one for work) because apps that have been enlightened to participate in the Intune MAM capabilities are now multi-user capable.
This feature also enables the full protection stack from identity to device, to apps, to files when used with O365, Azure AD, Intune, and Azure Rights Management (RMS).
Today was the first time Microsoft publicly discussed the multi-identity support coming to the Intune App SDK. This multi-identity support will enable apps to be used in both your personal and corporate lives.
- Microsoft’s commitment to Data Leakage Protection
This demo made it clear that Microsoft is committed to not only protecting against data leakage, abut also providing MAM for all platforms. The new Outlook app for iOS and Android, combined with the power of Intune and O365, is delivering on that commitment. - Our MAM strategy goes beyond “containers”
Not only does it extend beyond the idea of containers, it enables multi-identity-aware work and personal experiences that are relevant for real-world uses as well as the expectations users have when interacting with their apps. - Identifying corporate vs. personal apps/data
Not only is it now possible to identify corporate and personal apps and data on a device, but you can keep it separate – and you can do it all in a way that is seamless to the user. This prevents users from accidentally sharing sensitive data outside of the organization, and it allows IT to specifically define which apps have access to that corporate data. This also ensures that, when a device is wiped, only the corporate content is removed.
Coming soon
In addition, Microsoft announced
- Intune Conditional Access and Mobile Application Management for the Outlook app: This quarter, Intune will enable customers to restrict access to the Outlook app based upon device enrollment and compliance policies as well as restrict actions such as cut, copy, paste, and save as between the Intune-managed Outlook app and personal apps. Stay tuned to the Intune blog for more information on this feature when it becomes generally available.
- Azure AD Cloud App Discovery: In the next month Azure AD will enable customers to identify cloud apps being used in a customer’s IT environment revealing shadow IT. Read more from our engineering team about Cloud App Discovery.
- Public preview of Azure AD Privileged Identity Management: Enables customers to discover, restrict and monitor privileged accounts and their access to resources and enforce on-demand temporary administrative access when needed. Azure AD Privileged Identity Management is available in Azure AD Premium. Read more from our engineering team about Privileged Identity Management.
- Public preview of Azure Rights Management Document Tracking: Enables customers to track activities on sensitive files that they have shared with others. With a single click, users can also revoke access to shared files. Read more from our engineering team about Document Tracking.
Custom OMA-URI for Windows 10
Additionally, you can now create custom policies using OMA-URI to manage new Windows 10 features with Intune. As part of our monthly cloud cadence, we also plan to incrementally add native UI support for new Windows 10 features to provide you with best-in-class management for Windows 10 with Intune.
You can find more information on custom OMA-URI settings for Windows 10 here. This list of settings will continue to be expanded over time. You can also view the complete list of Configuration Service Providers (CSPs) exposed in the Windows 10 Technical Preview builds here.